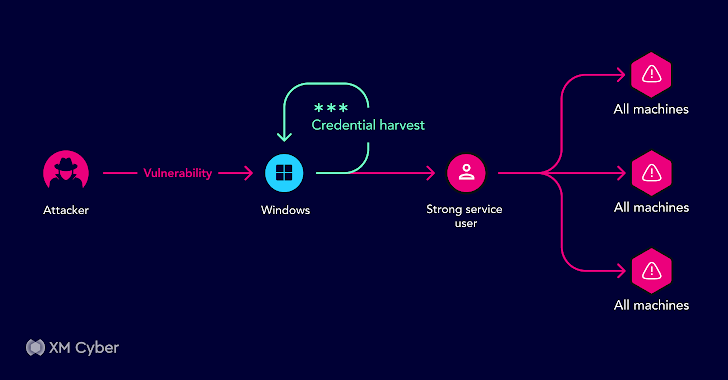
In the ever-evolving landscape of cybersecurity, attackers are always searching for vulnerabilities and exploits within organizational environments. They don’t just target single weaknesses; they’re on the hunt for combinations of exposures and attack methods that can lead them to their desired objective.
Despite the presence of numerous security tools, organizations often have to deal with two major challenges; First, these tools frequently lack the ability to effectively prioritize threats, leaving security professionals in the dark about which issues need immediate attention. Second, these tools often fail to provide context about how individual issues come together and how they can be leveraged by attackers to access critical assets. This lack of insight can lead organizations to either attempt to fix everything or, more dangerously, address nothing at all.
In this article, we delve into 7 real-life attack path scenarios that our in-house experts encountered while utilizing XM Cyber’s Exposure Management Platform in customers’ hybrid environments throughout 2023. These scenarios offer valuable insights into the dynamic and ever-changing nature of cyber threats.
From intricate attack paths that require multiple steps to alarmingly straightforward ones with just a few steps, our research unveils a staggering reality: 75% of an organization’s critical assets can be compromised in their current security state. Even more disconcerting, 94% of these critical assets can be compromised in four steps or fewer from the initial breach point. This variability underscores the need for the right tools to anticipate and thwart these threats effectively.
Now, without further ado, let’s explore these real-life attack paths and the lessons they teach us.
Customer: A large financial company.
Scenario: Routine customer call.
Attack Path: Exploiting DHCP v6 broadcasts to execute a Man-in-the-Middle attack, potentially compromising around 200 Linux systems.
Impact: Compromise of numerous Linux servers with potential for data exfiltration or ransom attacks.
Remediation: Disabling DHCPv6 and patching vulnerable systems, along with educating developers on SSH key security.
In this scenario, a large financial company faced the threat of a Man-in-the-Middle attack due to unsecured DHCP v6 broadcasts. The attacker could have exploited this vulnerability to compromise approximately 200 Linux systems. This compromise could have resulted in data breaches, ransom attacks, or other malicious activities. Remediation involved disabling DHCPv6, patching vulnerable systems, and enhancing developer education on SSH key security.

Customer: A large travel company.
Scenario: Post-merger infrastructure integration.
Attack Path: Neglected server with unapplied patches, including PrintNightmare and EternalBlue, potentially compromising critical assets.
Impact: Potential risk to critical assets.
Remediation: Disabling the unnecessary server, reducing overall risk.
In this scenario, a large travel company, following a merger, failed to apply critical patches on a neglected server. This oversight left them vulnerable to known vulnerabilities like PrintNightmare and EternalBlue, potentially jeopardizing critical assets. The solution, however, was relatively straightforward: disabling the unnecessary server to reduce overall risk.

Unlock cloud security insights with our eBook, “The Power of Attack Paths in Cloud.” Learn to visualize and cut off attack routes, safeguarding critical assets. Bridge Security and IT teams for swift remediation. Elevate your cybersecurity game today!
Customer: A large healthcare provider.
Scenario: Routine customer call.
Attack Path: An attack path leveraging authenticated users’ group permissions to potentially grant domain admin access.
Impact: Complete domain compromise.
Remediation: Prompt removal of permissions to modify paths.
In this scenario, a large healthcare provider faced the alarming prospect of an attack path that exploited authenticated users’ group permissions, potentially granting domain admin access. Swift action was imperative, involving the prompt removal of permissions to modify paths.

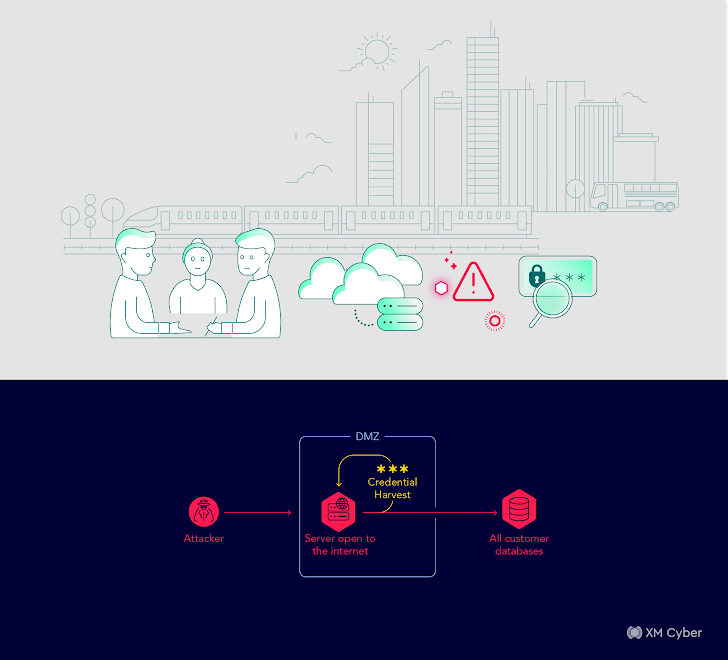
Customer: A global financial institution.
Scenario: Routine customer call.
Attack Path: Complex path involving service accounts, SMB ports, SSH keys, and IAM roles, with potential to compromise critical assets.
Impact: Potentially disastrous if exploited.
Remediation: Swift removal of private SSH keys, resetting IAM role permissions, and user removal.
In this scenario, a global financial institution faced a complex attack path that leveraged service accounts, SMB ports, SSH keys, and IAM roles. The potential for compromise of critical assets loomed large. Swift remediation was necessary, involving the removal of private SSH keys, resetting IAM role permissions, and user removal.
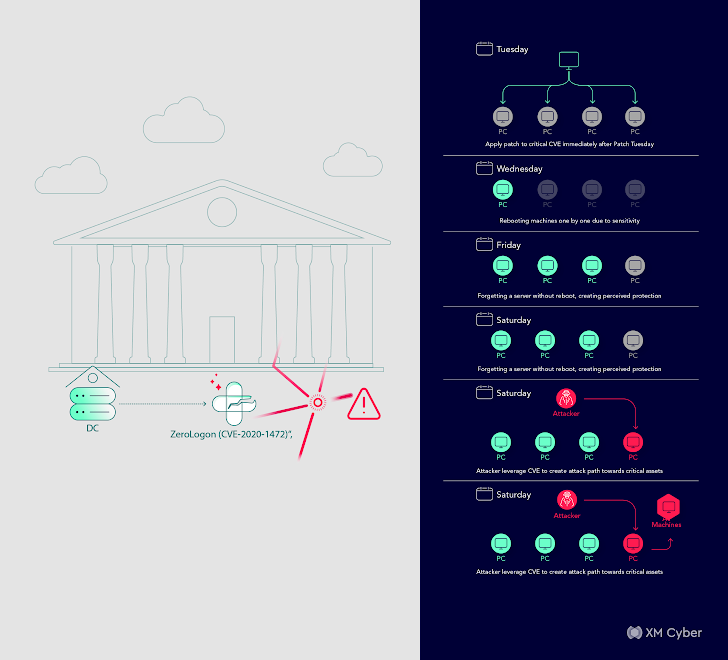
Customer: A public transportation company.
Scenario: Onboarding meeting.
Attack Path: Direct path from a DMZ server to domain compromise, potentially leading to domain controller compromise.
Impact: Potential compromise of the entire domain.
Remediation: Restricting permissions and user removal.
In this scenario, a public transportation company discovered a direct path from a DMZ server to domain compromise, which could have ultimately led to the compromise of the entire domain. Immediate remediation was crucial, involving the restriction of permissions and user removal.
Customer: A hospital with a strong focus on security.
Scenario: Routine customer call.
Attack Path: Active Directory misconfiguration allowing any authenticated user to reset passwords, creating a wide attack surface.
Impact: Potential account takeovers.
Remediation: Active directory security hardening and a comprehensive remediation plan.
This scenario unveiled a hospital’s vulnerability due to an Active Directory misconfiguration. This misconfiguration permitted any authenticated user to reset passwords, significantly expanding the attack surface. Remediation necessitated active directory security hardening and the implementation of a comprehensive remediation plan.

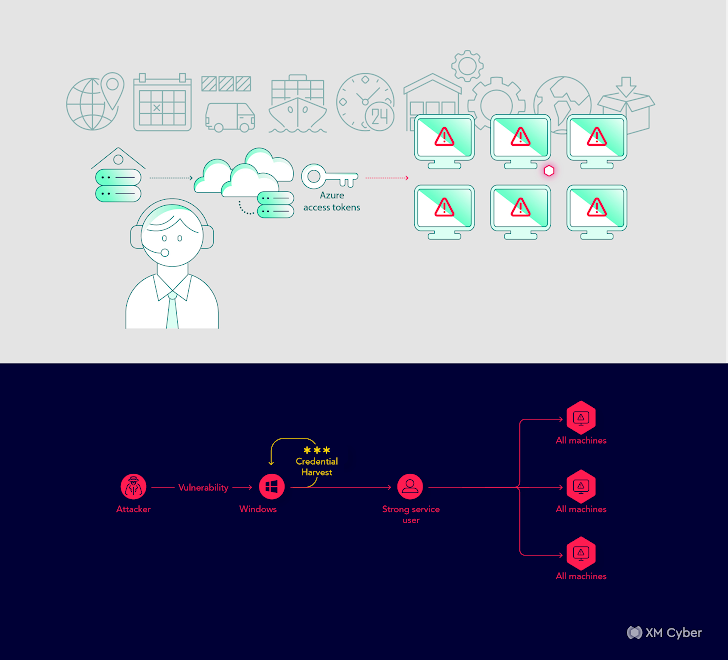
Customer: A major shipping and logistics company.
Scenario: Routine customer call.
Attack Path: An intricate attack path from a workstation machine to Azure, potentially compromising the entire enterprise environment.
Impact: Potential compromise of the entire enterprise environment.
Remediation: User role adjustments and issue remediation.
In this scenario, a major shipping and logistics company uncovered an intricate attack path that could have allowed attackers to compromise the entire enterprise environment. Remediation required adjustments to user roles and the thorough remediation of identified issues.
The common thread in these scenarios is that each organization had robust security measures in place, adhered to best practices, and believed they understood their risks. However, they often viewed these risks in isolation, creating a false sense of security.
Luckily these organizations were able to gain a context-based understanding of their environments with the right tools. They learned how various issues can and do intersect and thus prioritized necessary remediation’s, to strengthen their security posture and mitigate these threats effectively.
Reference: https://thehackernews.com/2023/10/unraveling-real-life-attack-paths-key.html